BitLocker is a mechanism that appeared with Windows Vista offering full disk encryption. If it was initially reserved for Pro editions, it is now available in all editions of Windows 11. On the most recent machines, it is even activated by default, a decision by Microsoft which communicated on this subject last May. This switch occurred with new installations of Windows 11 equipped with the latest major 24H2 update.
Encryption is based on 128 or 256 bit XTS-AES. In theory, it makes it possible to protect the information stored on the disk by requiring the possession of a key to decrypt it. This key is stored in the TPM chip (version 1.2 minimum). It must be the subject of particular care in the case of a reinstallation of Windows, so as not to lose its documents and other personal files, as we indicated last year.
However, this protection is not absolute. In February 2024, a YouTuber – Stacksmasher – showed how he was able to bypass BitLocker with less than $10 worth of hardware. The demonstration was impressive, but relied on a specific configuration. The computer had to have an LPC (Low Pin Count) connector available, which was the case on old Lenovo laptops. The issue was also known and documented by Microsoft.
Hacker Thomas Lambertz, however, showed a few days ago that information could be accessed without this technique, even if physical access remains mandatory.
An old flaw brought up to date
On December 28, Thomas Lambertz showed his method during the Chaos Communication Congress which was recently held at the Chaos Computer Club (CCC), often presented as the largest hacker club in Europe.
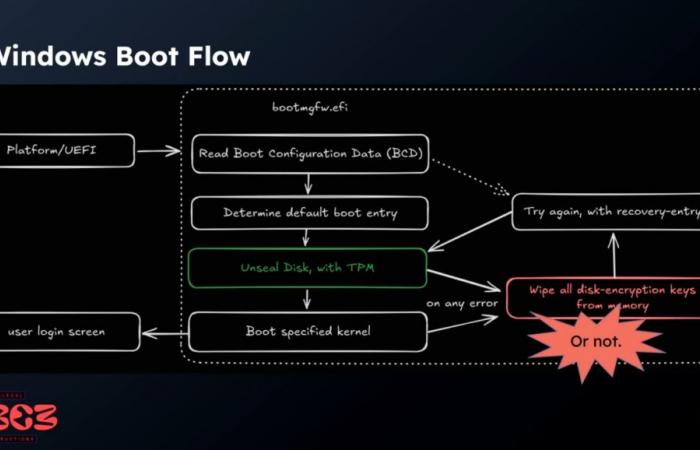
Its technique is based on an old flaw, CVE-2023-21563, also nicknamed “bitpixie”. In the Microsoft file, it appears as corrected in January 2023. Accompanied by a CVSS score (3.1) of 6.8, its dangerousness was set to “significant”. Exploited, it would have allowed a bypass of BitLocker and therefore access to data, even if it required physical access.
In his demonstration, Lambertz explains that this flaw could still be exploited, the correction not having covered all angles. To do this, the hacker redirected the Secure Boot mechanism to make it launch an obsolete bootloader for Windows. The loader’s mission is to extract the encryption key into memory, allowing an installed Linux system to recover it.
The procedure is as follows:
- Create a bootable USB key, whose storage space is greater than the amount of RAM on the targeted computer
- Suddenly restart the computer while Windows is starting, before the login screen appears, so that the encryption key is loaded into memory
- Boot from the USB key then load a custom UEFI shell, so you can run tools that will dump the memory
- Analyze dumps with tools like xxd and searchMem to locate the encryption key in specific areas
Exploiting this flaw is only possible because a full fix requires a change to UEFI. Microsoft would have been “stuck” by the limitations of storage space in this crucial component.
Variable danger
The whole question is how dangerous the technique used by Thomas Lambertz is. In absolute terms, it is: BitLocker is bypassed and previously encrypted information can be read. There are, however, two important conditions. On the one hand, physical access to the machine, which is far from being a guarantee, especially since you need to have time to carry out the manipulations. On the other hand, access to the network, via a USB adapter authorizing PXE booting.
It is likely that traditional users are not in danger. On the other hand, businesses, administrations and governments – particularly high-ranking members – should see it as a risk. If the operation cannot be carried out discreetly, the theft of the device remains possible. Stealing a celebrity’s laptop can lead to sensitive or even classified information.
Complete correction is not simple
To correct the problem, we must wait for a more lasting solution than the fix proposed by Microsoft two years ago. Unfortunately, this complete fix requires a replacement of security certificates, the revocation of which is not possible in a simple manner.
According to Thomas Lambertz, the publisher is aware of the problem, but is in a delicate position, since “ every firmware update it doesn’t predict correctly could break BitLocker. That’s why they don’t do it ».
What to do to protect yourself? There are few truly reliable methods. If Windows PCs running BitLocker are managed by an administrator, enabling the rule adding a PIN to unlock BitLocker is an important step. But for the hacker, there is only one way to block the problem at the root: “ The only thing you can do to prevent this attack is to disable the entire network stack in the BIOS. In this way, PXE boot is not possible, regardless of the device plugged in ».
In the meantime, the hacker’s technique is effective on any up-to-date Windows 11 machine. Microsoft has not yet reacted to these discoveries, but has been kept informed of the progress by Thomas Lambertz.