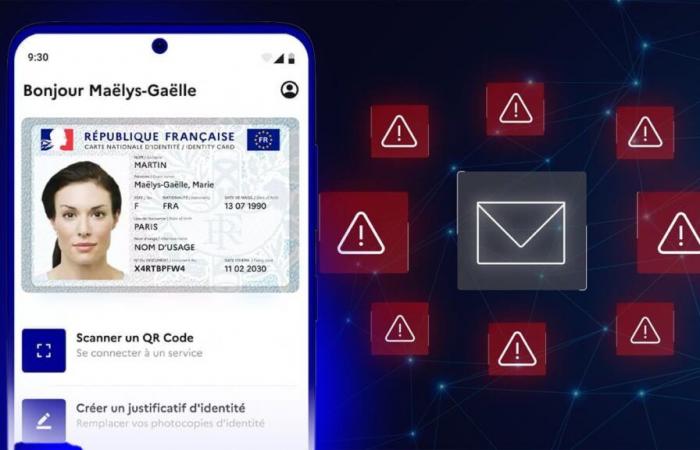
A new wave of phishing targets France Identity users
Users are encouraged to remain vigilant against emails that appear to come from official sources but are actually phishing attempts.
These fraudulent emails often ask recipients to provide personal and sensitive information, such as copies of ID cards or proof of address, under the guise of security checks.
How do fraudsters operate?
Scammers use sophisticated techniques to deceive their victims. They send emails from addresses that imitate those of official institutions, such as [email protected]to give an appearance of legitimacy to their requests.
To read
Here's how to deal with increased risks when shopping online while still taking advantage of the best deals
The content of these messages is often alarmist, urging recipients to act quickly, which is a common tactic to push victims to rush and prevent them from taking the time to verify the legitimacy of the requests.
The risks associated with phishing
The consequences of phishing can be serious. Stolen personal information is often used to commit more complex frauds, such as identity theft or financial fraud.
Once fraudsters have your personal data, they can exploit it in multiple ways, increasing the risk of financial and reputational damage.
Understand the changes and steps for your retirement this year
Recognizing the signs of a phishing email is crucial to protecting yourself against these scams. Clues like suspicious email addresses, spelling mistakes, and an overly urgent tone can all be red flags.
Tips to avoid falling into the trap
To protect against these attacks, it is essential to scrupulously verify the origin of any email requesting personal information. Never clicking on links or downloading attachments from unknown or suspicious sources is a golden rule.
Here are some recommended actions to strengthen your security:
To read
Agirc-Arrco increase in November 2024: what impact on your retirement pension?
- Always check the sender's address and compare it to official communications.
- Never respond directly to emails that seem suspicious.
- Contact the organization through a verified means to confirm the authenticity of the request.
By following these simple steps, you can significantly reduce the risk of becoming the next phishing victim. Maintaining a critical eye and healthy skepticism when faced with requests for personal information is your best defense against cybercriminals.
Caution is advised and it is recommended to stay informed of the latest tactics used by fraudsters to continually improve your personal security measures. Knowledge and vigilance are the keys to effectively combating phishing.